Lightrun persona-based role management overview🔗
Starting with version 1.70.4, Lightrun replaces its previous role system with a persona-based role mechanism, providing finer-grained control over resources and user actions, improving security, and operational clarity.
This approach aligns permissions with common organizational personas—such as Developers, Company Admin, and Security—allowing administrators to:
- Delegate tasks precisely.
- Enforce least-privilege access.
- Reflect real job functions across both the plugin and Management Portal.
Each role is composed of one or more categories, and each category contains predefined permissions at specific access levels. Assigning a role grants all associated permissions, giving precise control over the actions a user can perform. Roles are predefined to reflect common organizational personas.
Lightrun supports role assignment in both RBAC (Role-Based Access Control) and non-RBAC environments:
- Non-RBAC environments: Offer only two basic roles:
DeveloperandCompany Admin. -
RBAC environments: Provide a broader, predefined set of roles for finer-grained access control.
Example: The
Company Adminrole includes full management permissions at the company level, such as user administration, webhook creation, and authentication.
Migrating to persona-based roles🔗
To maintain compatibility with the previous role mechism, upgrading from versions prior to 1.70.3 or higher automatically converts existing roles to their persona-based equivalents:
- Users with the previous
default_userrole →Developerrole - Users with the previous
ROLE_MANAGERrole →Company Adminrole - Existing Group admins → Group Admin role (retain Environment-level administrative permissions)
Key benefits🔗
Better alignment with job functions🔗
Example: Developers can log in to the plugin and the Management Portal, while Company Admins perform management tasks such as configuring features, managing users, and maintaining Lightrun entities (e.g., agent pools, tags, and custom sources).
Finer control over what each user can see and do🔗
Example: Developers have Read (R) permissions to view PII redaction patterns, whereas Company Admins can create and manage those patterns.
More precise and flexible permission management🔗
Example: Group Admins (RBAC only) can manage access within their assigned Environment without affecting organization-wide settings, while Company Admins retain full control at the company level.
Reduced risk of granting unnecessary access🔗
Example: Company Viewers (RBAC-only) can access dashboards and logs for monitoring purposes without the ability to modify system configurations, keeping sensitive actions restricted.
Persona-based roles terminology🔗
Understanding the following terms is important for working with Lightrun’s persona-based role system.
Company🔗
The top-level organizational unit in Lightrun. All users and configurations belong to a company.
Role🔗
Roles are preset and predefined in Lightrun. A user can have multiple roles, and all permissions from those roles apply. If roles overlap, the highest permission level takes precedence.
Example: A user assigned both the Developer and Company Admin roles inherits permissions from both, but the broader Company Admin permissions override where conflicts exist.
Category🔗
A collection of related operations with permissions. Roles include one or more categories that define the actions a user can perform.
Permissions🔗
Predefined access levels that control what a user can do within a category. Permissions cannot be modified or removed.
- Read (R): View information without making changes.
- Write & Read (WR): View and modify information.
Understanding persona-based roles🔗
Each role is composed of one or more categories, and each category contains permissions at specific access levels. Assigning a role to a user grants all associated permissions, ensuring precise control over user actions.
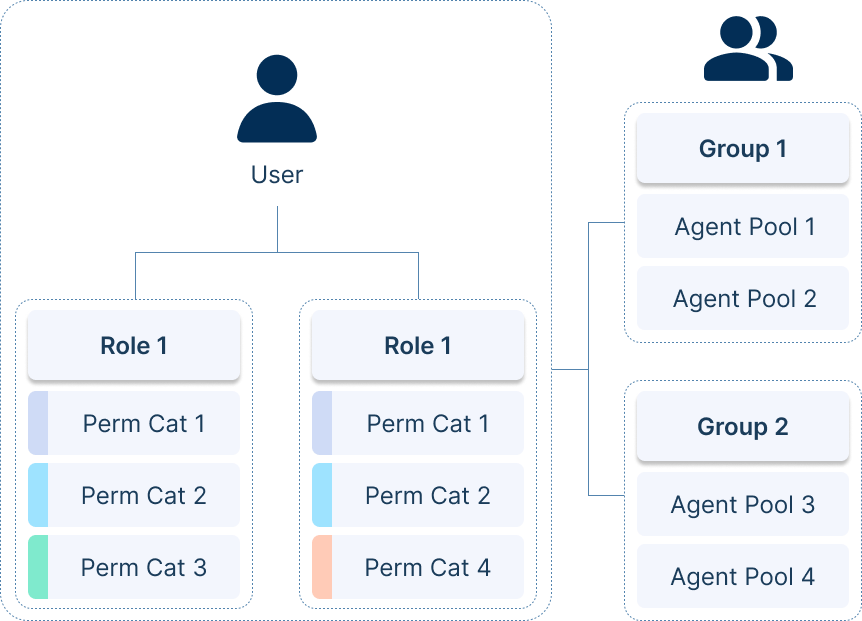
Roles are preset and designed to reflect common organizational personas such as Developer, Company Admin, Security, and Group Admins.
Example: The Company Admin role includes full management permissions at the company level, such as user administration, webhook creation, and authentication.
Built-in roles and categories🔗
Lightrun roles are predefined and aligned with common organizational personas. The table below provides a high-level overview of all roles and their scope.
Built-in roles🔗
| Role | Role capabilities | Environment |
|---|---|---|
Developer | Access runtime diagnostics and observability. | Non-RBAC & RBAC |
Company Admin | Full administrative control at the company level. | Non-RBAC & RBAC |
Company Viewer | Read-only access to company-wide settings. | RBAC only |
Group Admin | Manage user groups and related resources. | RBAC only |
Security | Manage Security configurations and audit controls. | RBAC only |
AppSec | Manage application Security features. | RBAC only |
Incident Responder | Resolve cases, configure debugging runbooks, and review case results. | RBAC only |
Predefined role categories🔗
Each role is composed of one or more categories that define the functional areas in which users can operate. Understanding these categories clarifies what permissions a role grants.
| Category | Description | Audience |
|---|---|---|
Company config | Company-level settings and user management | Company Admin |
Security | Controls for protecting data, audit events, PII redaction, blocklists | IT Specialists |
Environment | Runtime spaces such as agent pools, dashboards, debugger configurations | Company Admin |
AppSec | Application Security monitoring, Runtime Reachability | AppSec / Company Admin / Company Viewer |
Debugging Runbooks | Tools for tracking, managing, and resolving cases, uploading configs, viewing case results | Company Admins and developers |
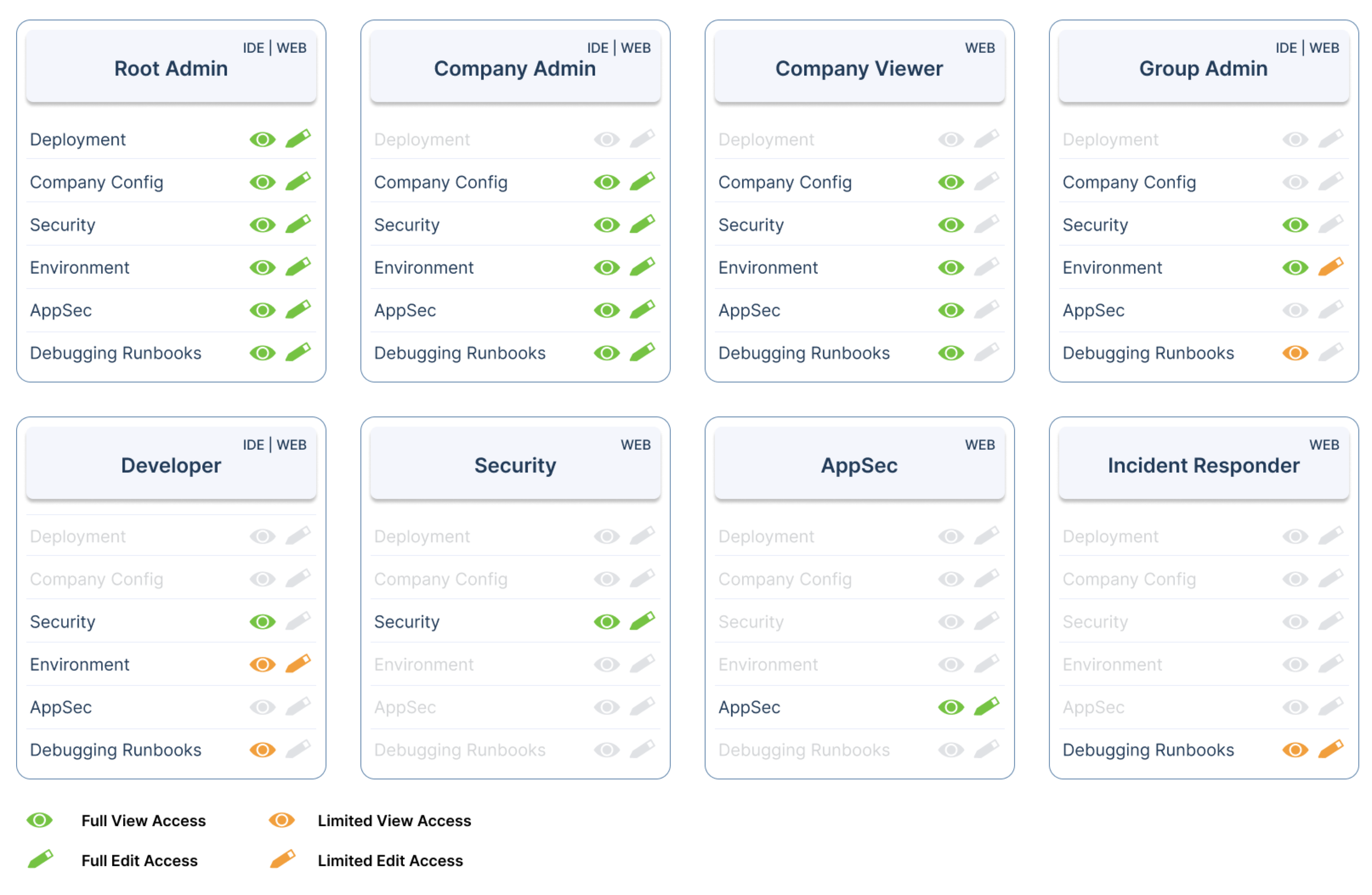
Roles cheat sheet🔗
The following matrix provides a detailed mapping of how each predefined role corresponds to categories and the specific permissions included within those categories. This mapping clarifies the access granted to users based on their assigned role.
Use this summary matrix for quick reference.
Get started🔗
Start creating users with assigned roles:
- Create users with roles in an RBAC environment.
- Manage groups in an RBAC environment.
- Create users with role in a non-RBAC environment