Configure temporary access in Lightrun🔗
Version applicability
This topic applies to setting temporary access to Lightrun resources using the RBAC role mechanism, supported up to version 1.69 and earlier. To apply setting temporary access using persona-based roles, see Configure temporary access in Lightrun.
The Lightrun temporary access feature allows administrators to generate temporary time-bound permissions for accessing sensitive agent pools for predetermined periods. It provides an "as-needed" mechanism to grant time-limited access for specific users, which is useful for developers needing short-term access, such as on-call production support. Applying temporary access protects production environments while providing developers the agility they need to resolve critical issues or support customer needs promptly.
Temporary access is valuable for organizations with policies and regulations that restrict access to sensitive environments as it ensures permissions are granted only for the minimal necessary period. This capability allows these companies to automate the provision of elevated permissions and manage them with existing processes and systems external to Lightrun.
Lightrun supports the following methods for configuring temporary access:
- Configure temporary access in the Lightrun Management Portal
- Configure temporary access using Lightrun REST API
Rules and guidelines🔗
- User limit: Up to 50 users can be granted temporary access in a single grant.
- Number of simultaneous concurrent grants: A maximum of 100 concurrent temporary access grants are allowed simultaneously. Requests exceeding this limit will be denied.
- Access expiration period: Access rights should be time-bound, ensuring they are automatically revoked once no longer needed. Temporary access can be granted for a period of up to 31 days. Requests for a longer time period will be denied.
- Agent Pool limit per grant: A single temporary access session can grant access to a maximum of 20 agent pools.
- Least Privilege Principle: Users should be granted the minimum level of access necessary to perform their tasks.
- Users cannot be removed from an active temporary access instance. To exclude specific users, delete the instance and recreate it without including those users.
Prerequisite🔗
Do the following before configuring temporary access:
-
RBAC Security: Ensure that Role-Based Access Control (RBAC) features are enabled on your platform.
-
Agent Pools: Create the necessary agent pools for your engineering groups, as they will be used for debugging.
-
Agent Pool ID: You will need the Agent Pool ID when setting temporary access on agent pools.
To retrieve the agent-pool IDs, run the Get api/v1/agent-pool command to get a list of all agent pools.
Configure temporary access in the Lightrun Management Portal🔗
- Log in to your Lightrun account.
- Click Settings at the top right-hand side of your screen to navigate to the Settings dashboard.
- Navigate to Identity and Access Management > Permissions & Access.
-
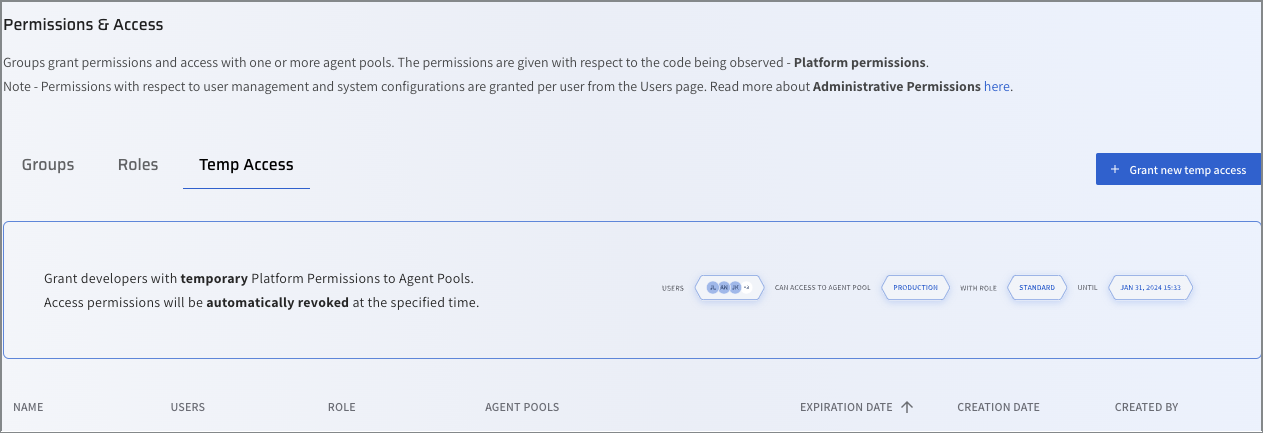
Click the Temp Access tab.
-
Click + Grant new temp access.
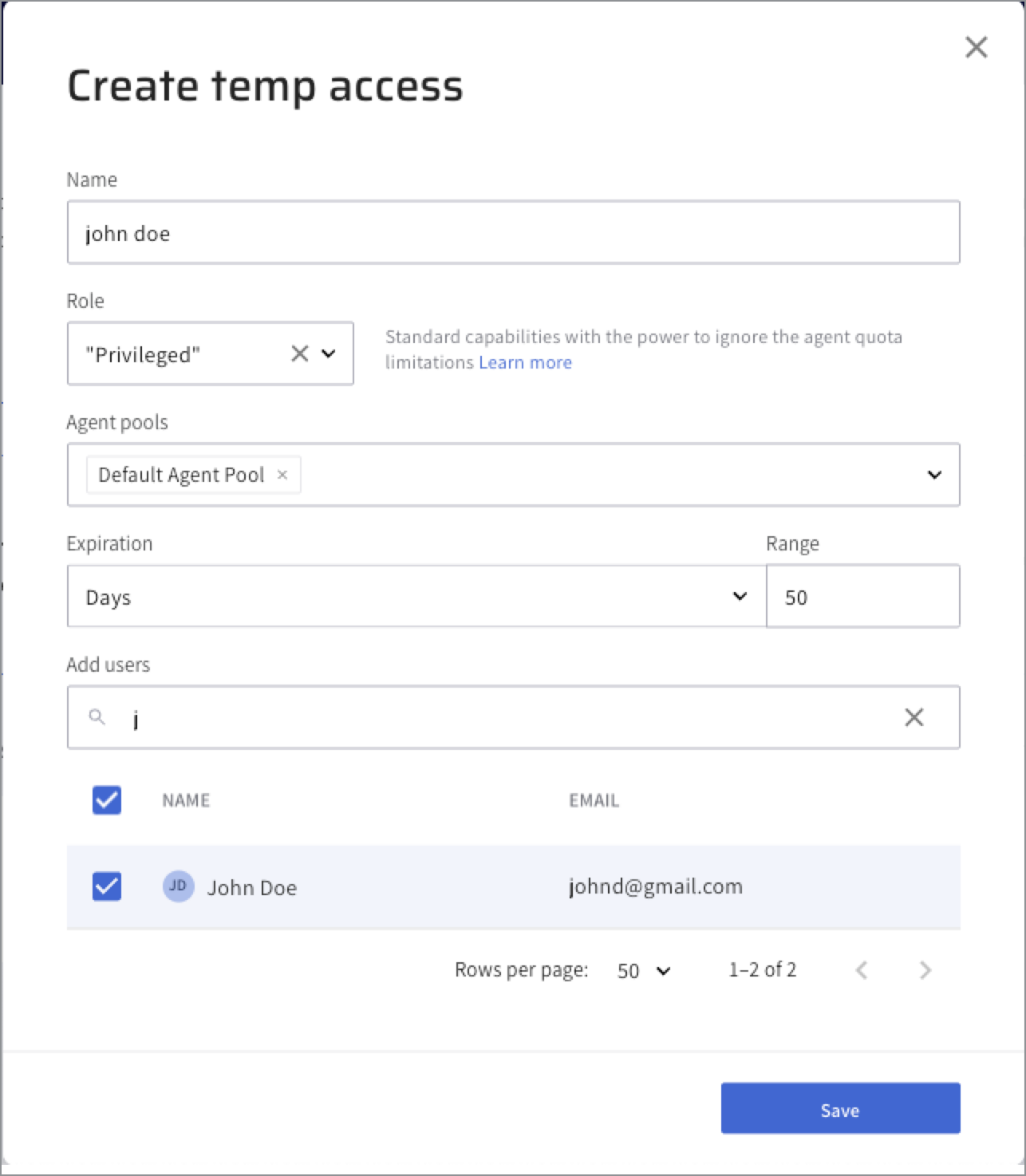
The Create temp access page opens.
-
In the Name field, provide an intuitive name for the temp access instance to help you identify and keep track. For example include the user name and expiration time or date.
-
In the Role field, assign a role that will be granted to all the users granted temporary access. Note that when the temporary access revokes, the users' roles will be revoked too.
The roles are identical to the RBAC roles and include:
- Standard Role: The standard role grants regular access to an agent pool. This includes creating Lightrun actions with the agents in the agent pool, full access to action data, etc..
- Privileged Role: The privileged role grants a group the ability to ignore agent quota limitations in addition to the permissions granted by the Standard role.
-
In the Agent pools field, grant access to agent pools resources, allowing users assigned to the temp pool to access them.
-
In the Expiration field, set the expiration time of the temporary access instance. You can set it by: Days, Hours or Custom. To provide more flexibility, you can choose Custom allowing you to select an Expiration Date or Expiration time.
-
In the Add users field, select users from your organization.
Tip: Use the search if you have many users in your organization. 11. Click Save.
Delete a JIT Access instance in the Management Portal🔗
An active JIT Access instance cannot be modified. We recommend deleting the active JIT Access instance in the Lightrun Management Portal and then recreate it.
- Log in to your Lightrun account.
- Click Settings on the top right-hand side of your screen to navigate to the Settings dashboard.
- Navigate to Identity and Access Management > Permissions & Access.
-
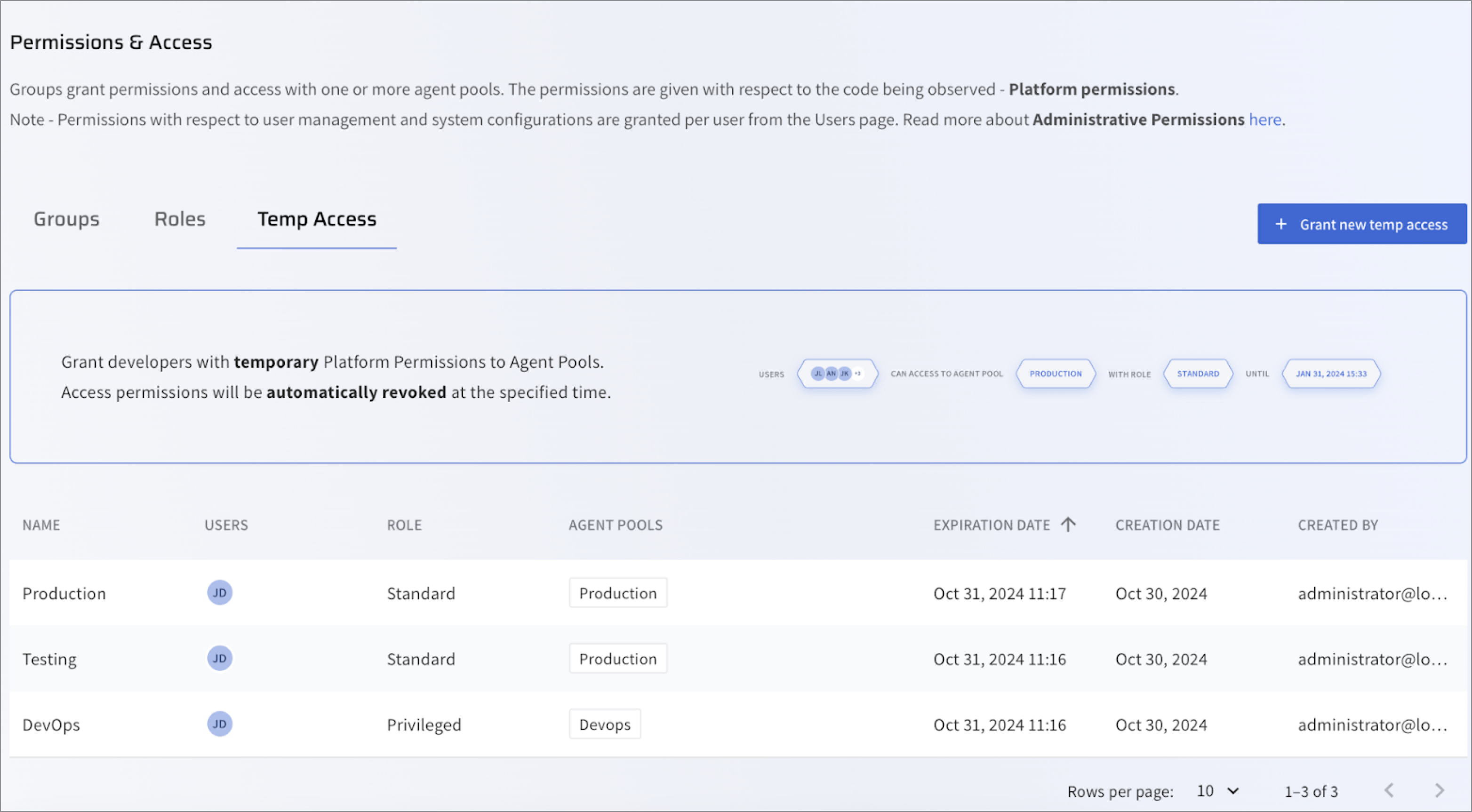
Click the Temp Access tab. The list of active Temp Access instances are displayed.
-
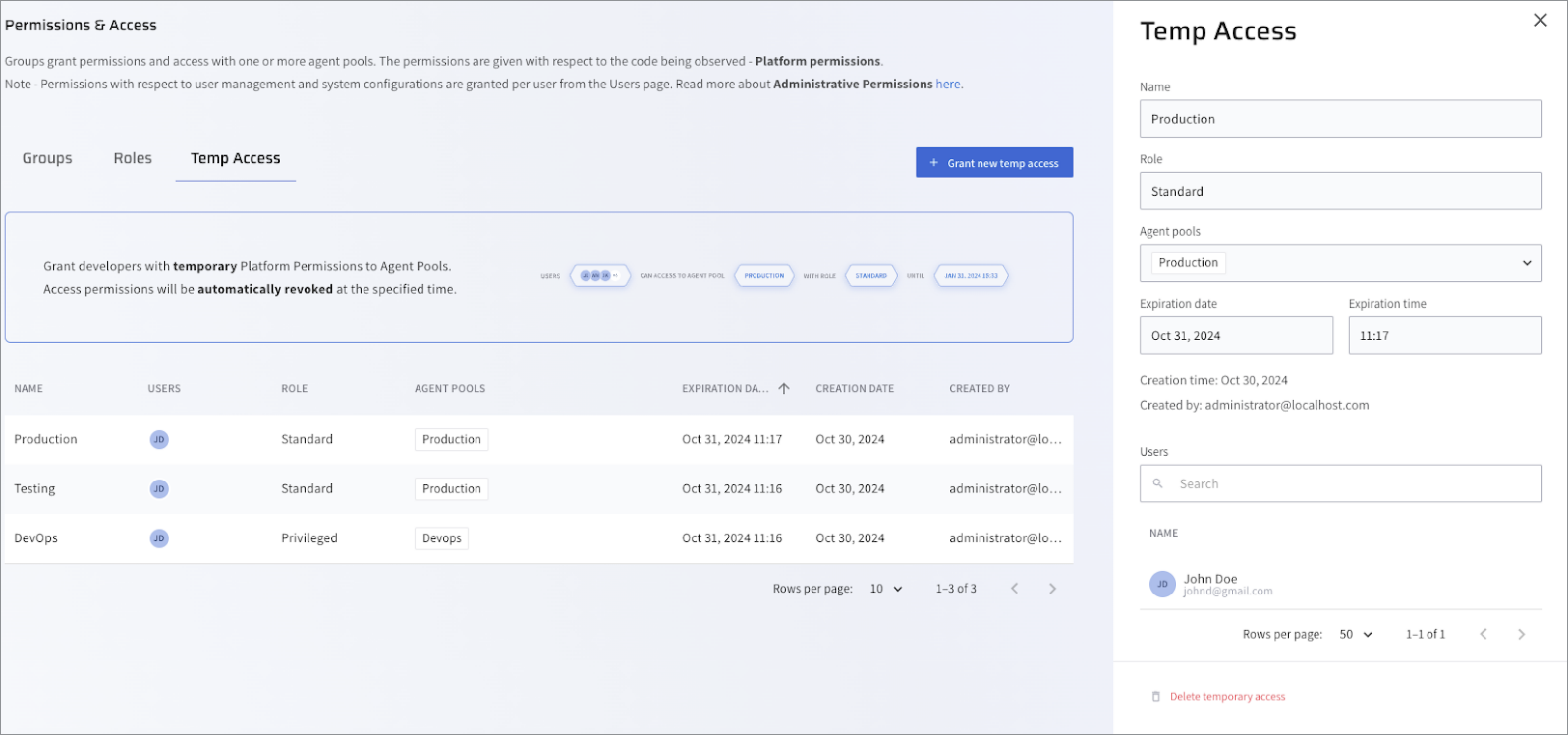
From the list, select an instance to be deleted. For example, Production.
-
Click Delete temporary access.
The JIT Access instance will be removed from the list.
Configure JIT Access with the Lightrun REST API🔗
The following JIT Access REST APIs are supported and are described in detail in the Lightrun REST API:
- Grant JIT Access REST API: Grants temporary access to the specific agent pool for the specified period of time.
- Revoke JIT Access REST API: Revokes JIT access to an agent pool.
- Get JIT Access List REST API: Retrieves a list of all active JIT accesses currently set in the organization.
To learn more about the Lightrun REST API conventions, see Lightrun public REST API.